ONLINE PREPAYMENT VENDING SYSTEM
1.AN EXECUTIVE SUMMARY OF THE TECHNICAL
1.1 Scope
According to requirements for Prepayment System, Hexcell is offering a total solution for power vending. This includes:
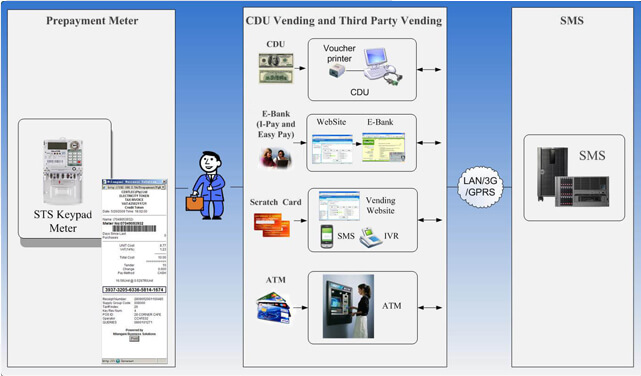
1.Multiple Vending including CDU, M-POS, UUSD, Third party vending;
2.Data analysis and Statistic;
3.Prepayment management;
4.Reports management;
5.Interface with Billing Systems;
6.Interface with other system for third party vending, such as E-Bank System, ATM System, Scratch Card system etc.
7.System implementation and Training;
The above strategy can provide the following advantages:
1.Easy Vending.
2.Improving revenue recovery.
3.Introducing state-of-the-art technology and modern management systems.
1.2 System Overview
Hexcell provides utilities a superior prepayment vending system, which features high flexibility and enhanced versatility. The system is designed to support in all aspects of electricity vending, revenue collection and customer management to suit growing needs of global market. It uses distributed and true browser‐server network, comprising two main parts:
1.entral system server (System Master Station, SMS);
2.ending station (Credit Dispensing Unit, CDU);
The system is Windows‐based and makes use of Local Area Network (LAN) and Wide Area Network (WAN) on the existing Internet infrastructure.
1.3 System Feature
1.3.1 International Standard Comply
The system is a multi-user multi - operating system catering multi-users’ requirement. The operating system is Windows2008 according to the standards IEEE and OSF; both SQL query language and C/C++ language are used as database access language in accordance with protocol ANSI. The network communication protocol is using TCP/IP protocol.
Hexcell Online Prepayment Vending system is the outcome of rich system experience. The system software is user – friendly and interactive. All the interface and operation process are developed based on user – friendly and facilitate user concept. All analysis result can be direct-viewing with great convenience.
The software is modular with appropriate set of menus to perform the pertinent functions.The operation interface is using secondary menu to facilitate operation.
1.3.2 Distributed Network Architecture
The distributed network architecture is using Client/Server model and with following features: high-efficiency running, fast response speed, great concurrent operation ability, completed function distribution mode.
1.3.3 General Hardware Platform
The general hardware platform of the system is compatible with a variety of hardware equipments, such as HP, IBM, DELL, Lenovo, Cisco, Nortel, EPSON.
1.3.4 System Stability And Reliability
The system supports following function to assure the stability and reliability:
1.FEC Fast Ethernet channel provides the up to four network link redundancy with1000 M bandwidth in the 100/1000 M exchange network.
2.The three databases (Original database, Application database, WEB database) can be in concentrated mode or separated mode physically or logically. When they are separated, the system efficiency and security can be improved; while concentrated mode can reduce the project investment. Both modes can ensure that the original database will not be modified, and improve the data security.
1.3.5 Expandability
System employs open distributed architecture to support following upgrade:
1.Seamless hardware upgrade
2.Mutual PC backup upgrade
3.Mutual NET backup upgrade
1.3.6 Easy Maintenance
1.Simplified system installation
2.User friendly interface
3.English and Arabian language interface
4.Menu-operation
5.Remote maintenance management
1.3.7 Data Security
This system employs 4-level safety control, which is to ensure the safe operation of the whole system and data security.
1.3.8 Database Security
The database will take password protection against unauthorized access. Different user is set with different security level accordingly.
1.3.9 Application Software Security
The application employs a variety of security design, first of all, is user authority management, for example, only system administrator can set user privileges, only the operator can process business operation.
System administrators are also divided into multi-level management architecture, super-administrator (the top security level) can authorize the affiliated system administrator (lower security level), and the system administrator can authorize the lower level administrators. Only super-user can view users operation and maintenance log.
1.3.10 System Backup
System backup will be auto executed periodically or manually in time.
All related system operation such as data modification should be performed by authorized stuff and recorded with operation time, operator ID and special mark.
